The EMu application must be registered with an identity provider such as Microsoft via Azure Active Directory (AD) and Google via Google Cloud Platform. Most EMu customers will probably find that Microsoft is the most convenient provider as this allows a user to be authorized to access the Windows desktop, Office 365 and EMu using the same credentials.
As registering an application with an identity provider requires privileged access, it is typically done by the customer. Once the EMu application has been registered, it is necessary to configure the EMu server to use OpenID. While configuring the EMu server to use OpenID can be performed by Axiell staff, this requires access to your organization's identity provider connection details (including your client_secret). As such it is highly recommended that your System Administrator configures the EMu server to use OpenID.
The requirements for registering an application with an identity provider and the registration information that must be provided to Axiell can be different depending on the identity provider. Differences for Microsoft Azure AD and Google Cloud Platform are highlighted below.
Tip: An example of registering the EMu application on the Microsoft Azure AD identity platform is provided below.
There are three main considerations when registering the EMu application (reviewing the example registration below should clarify what is required):
|
# |
Consideration |
Details |
|---|---|---|
|
1 |
Desktop application registration |
The registration should be configured for a desktop or public client / application. For example, when configuring the Redirect URI in Microsoft Azure AD you would select: Public client / native (mobile & desktop) |
|
2 |
Specify the Redirect URI |
The Redirect URI itself must be:
Differences between Microsoft and Google:
|
|
3 |
Specify access to the required scopes |
Scope values specify the user information that the application is allowed to access. Access to the following scopes is required:
Details about scope values can be found on the Microsoft documentation site: Permissions and consent in the Microsoft identity platform. Differences between Microsoft and Google:
|
Full details about registering an application with Microsoft and Google are available here:
Once the EMu application has been registered with an identity provider, it is necessary to configure the EMu server to use OpenID. While configuring the EMu server to use OpenID can be performed by Axiell staff, this requires access to your organization's identity provider connection details (including your client_secret). As such it is highly recommended that your System Administrator configures the EMu server to use OpenID.
Details about how to configure the EMu server to use OIDC can be found here.
Alternatively, Axiell staff can undertake the server configuration for you. In this case, information must be obtained from the application registration and provided to Axiell. This may include:
- Application (client) ID
- OAuth 2.0 authorization endpoint (v2)
- OAuth 2.0 token endpoint (v2)
- OpenID Connect metadata document
The following information may need to be obtained from the application registration and provided to Axiell:
- Application (client) secret
This information is used by Axiell to configure a customer's EMu client and server to use the OIDC protocol.
Differences between Microsoft and Google:
Microsoft:
- Microsoft Azure AD uses specific endpoint and metadata document values for each organization (AKA tenant). These values must be provided to Axiell.
- Microsoft Azure AD does not use or provide the Application (client) secret value for registered desktop or public applications. Therefore, it is not necessary to provide this value to Axiell.
Google:
- It appears that Google Cloud Platform uses the same endpoint and metadata
document values for all organizations, specifically:
- Authorization endpoint:
https://accounts.google.com/o/oauth2/v2/auth
- Token endpoint:
https://oauth2.googleapis.com/token
- Metadata document:
https://accounts.google.com/.well-known/openid-configuration
- Authorization endpoint:
- Google Cloud Platform requires the use of the Application (client) secret value when authorizing registered desktop applications. Therefore, this value must be provided to Axiell.
The steps are:
- Sign into the Azure portal.
- If you have access to multiple tenants, use the Directory + subscription filter in the top menu to select the tenant in which you want to register an application.
- Search for and select Azure Active Directory.
- Under Manage, select App registrations>New registration.
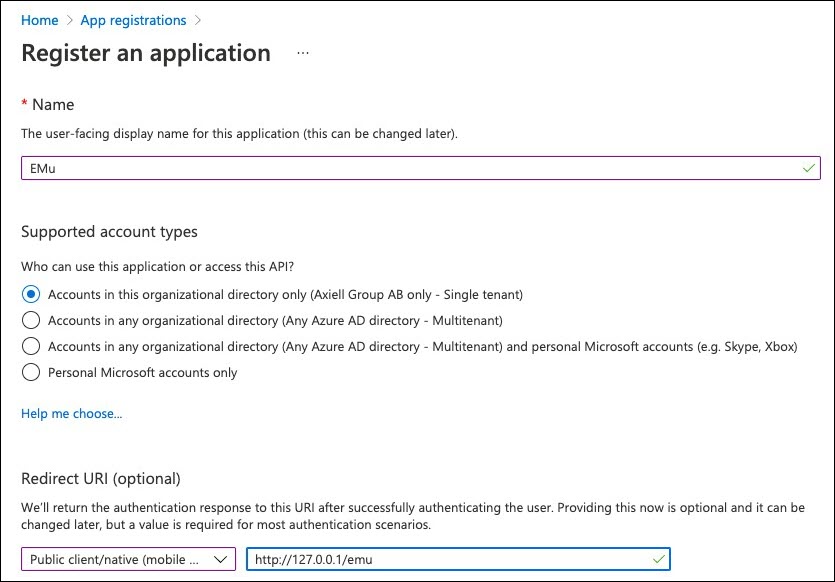
- Set the application Name:
EMu - Set the Supported account types.
The value for this setting depends on the Azure AD setup but is likely to be:
Accounts in this organizational directory only (Axiell Group AB only - Single tenant)
- Set the Redirect URI.
It should be specified for:
Public client/native (mobile & desktop)
And the Redirect URI should have the value:
http://127.0.0.1/emuSee the following screenshot for an example:
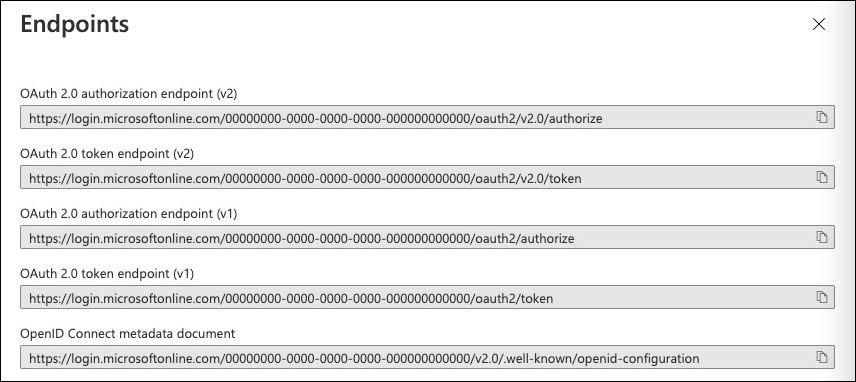
- Obtain the registration details.
To configure the EMu client and server to use OIDC, some information about the application registration must be provided to Axiell. The required information is:
- Application (client) ID
- OAuth 2.0 authorization endpoint (v2)
- OAuth 2.0 token endpoint (v2)
- OpenID Connect metadata document
The Application and Directory IDs can be found on the Overview page of the Application Registration, for example:
The endpoint and metadata document information can be found on the Endpoints page accessible via the Endpoints button on the Overview page of the Application Registration, for example: